NutNow you can listen to the Fox News items!
Online scams prosper on the urgency and fear of their victims. If you have ever been the victim of a scam, you would know that bad actors often try to hurry -you take measures by creating a sense of fear. A scammer can call -you are a government agency and claim that your Social Security number has been related to drug trafficking.
An email from Phishing may ask you to update the tax data or claim that you have won a free lottery or product, all to click on a malicious link.
The most effective tactical use of scammers is to send fake login alerts. These are warnings that someone has signed in to your account, asking -you do immediate measures. This method works well because legitimate services such as Google, Apple, Netflix and Facebook also send these types of notifications when someone, including you, logs in from a new device. It can be difficult to say the difference.
As Danville’s Robert asks, “I continue in the emails of my spam junk folder saying” someone has connected to your account “. Is it a spam?
UNIV: Get my expert technology tips, critical security alerts and exclusive offers, as well as instantaneous access to my Free Survival Guide to the definitive scam When you register!
Thank you for writing, Robert. I fully understand the complicated one that may be to find out if these messages are legitimate or only another scam attempt. We break down what these urgent warnings often seem to be and exceed some ways to keep in security.
A person who is recorded in a gmail account on a laptop (Kurt “Cyberguy” Knutsson)
How the login alert scams work and why they are so effective
The scammers are usually considered as Google, Apple, Meta or even your bank’s login alerts, completed by official-looking logos, because fear is effective. But not all alerts are a scam. In many cases, these notifications are legitimate and can help you detect unauthorized access to your accounts. We focus -first on the side of the scam.
Login alert scams have been for a while. The first reports date back to 2021, and the trend has since persisted. By 2022, reports appeared that the scammers meant a goal and sent phishing emails to users.
The FBI warns the scam aimed at victims with fake hospitals and police
One of these emails used a net design with minimal text. He avoided the usual scare tactics and stuck to a simple message. But this is not always the case. A red flag common at phishing attempts is the tendency to overload the email with unnecessary details. These messages often include a messy format, excessive explanations and an increasing number of design or design errors. A phishing email simply reaches the point:
Someone tried yog to your account, LD user
A user has just logged on to your Facebook account from a new Samsung S21 device. We send you this email to verify that you are really you.
Thanks,
The Facebook team
What it is now is that the poor grammar is no longer a reliable sign of a scam. Thanks to AI, even those with limited English skills can write emails that seem polished and professional. As a result, many phishing messages today are read just like the legitimate emails of trusted companies.
Receiving a phishing email is not the real problem. The actual problem starts when clicking it. Most of these emails contain links that lead to fake login pages, designed to look exactly like platforms like Facebook, Google or your bank.
If you enter your credentials there, go directly to the scammer. In some cases, simply clicking on the link may trigger a malware download, especially if the browser is outdated or the device is not properly safe. Once inside, attackers can steal personal information, control your activity or control your accounts.

Illustration of a hacker at work (Kurt “Cyberguy” Knutsson)
Don’t click this link! How to detect and prevent phishing attacks on the inbox
How to know if a login alert is real or false
Real login notifications do exist; They are much less scary. A real alert from Google, Apple or Microsoft will come from an official address (for example, non-rely@accouunts.google.com or security@apple.com) and use a consistent brand. The tone is factual and helpful.
For example, you can say a legitimate alert of Google Security, “”We detected a login from a new login on your Google account on a Pixel 6 Pro device. If you are you, you don’t have to do anything. If not we will help you secure your account. “” It may include a “activity check” button, but this link always redirects to a Google.com address and will not ask you to re -enter your password using the email link. Similarly, Apple Notes will never ask for passwords or email verification codes.
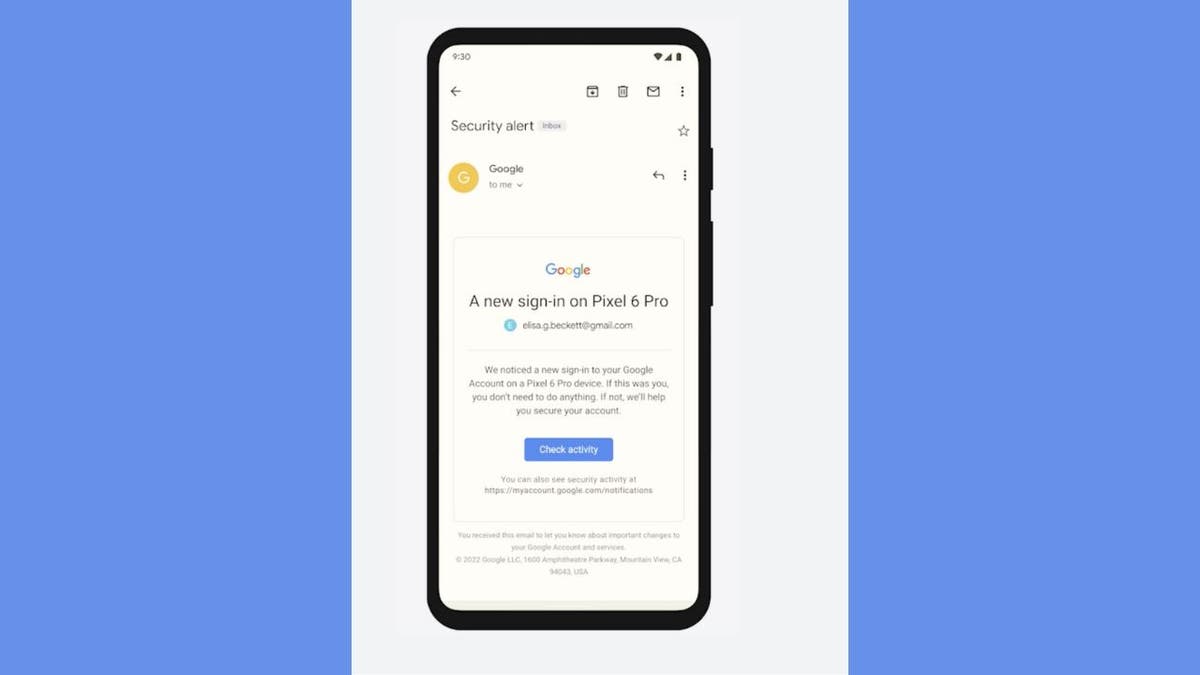
Google legitimate notification (Google)
The FBI warns the scam aimed at victims with fake hospitals and police
What do you need to do if you get an email from suspicious login alert
1. Do not click any links or attachments and use a strong antivirus software: Instead, manually log in to the real site (or open the official application) by writing the URL or using a marked link. This guarantees that you do not walk in a scammer’s trap. FTC recommends this: If you have an account with this company, please contact them through the website or the phone number you know is real, not The information in the email.
The best way to safeguard the malicious links that install malicious software, which can potentially access your private information, is to install antivirus software on all your devices. This protection can also alert you to Phishing emails and ransomware scams, maintaining safe personal information and digital assets. Get my options for the best antivirus 2025 protection winners for your Windows, Mac, Android and iOS devices.
2. Eliminate your Internet details: The scammers can send -you messages oriented so that your data, such as your email address or phone number, are already out. This is often the case due to past data breaches and shady data agents. A data removal service can help clean your digital trail by removing public database information and people’s search sites. It is not a quick solution, but over time, it reduces the ease that scammers can find and guide -you.
While no service can guarantee complete deletion of your Internet data, a data removal service is really a smart choice. They are not cheap and not your privacy. These services do all the work to systematically control and clear the personal information of hundreds of websites. It is what gives me peace of mind and has proven to be the most effective way to delete your personal Internet data. By limiting the available information, reduce the risk of reference fraudster to breaches with information they could find on the dark network, which makes them more difficult to guide you. Check out my best options for data removal services here.
Get Fox Business during clicking here
Get a Free Exploration To know if your personal information is already on the net.
3. Check your account activity: Go to your account safety page. Services such as Gmail, ICloud or your bank allow you to review recent session starts and devices. If you see nothing unusual, you are sure. If you find a strange login, follow the site process (usually change the password and session of all devices). Even if you don’t find anything weird, change your password as a precaution. Fifth through the official site or app, not email. Think of using a Password manager to generate and store complex passwords.
4. Activate the authentication of two factors (2f): This is your best backup. With 2fa Activated, even if someone has your password, cannot access without the phone and an additional second factor. Both Google and Apple facilitate 2f and say “it makes it harder for scammers to” sequest your account.
5. Report suspicious emails: If you receive a suspicious email calling for a specific organization, inform the organization’s security team or to the organization’s safety team so that they can take appropriate actions.
This is what you are doing wrong when the scammers call
Kurt’s Key Takeaway
You should not have to ensure all the emails. In fact, spam filters of your email catch most of phishing attempts. Keep your skills and ensure -You’s that your software is updated so that malicious attachments and attachments are blocked. However, the most powerful filter is your own conscience. You are definitely not alone in this. People receive these spam session breakwaters every day. If you keep a fresh head and following the previous steps, you are already ahead of the game.
Click here to get the Fox News app
Have you ever found an email or suspicious phishing attempt? How did you do it, and what did you learn from experience? Make -us to know by writing -us to Cyberguy.com/contact
For more information on my technological and safety alerts, subscribe -you are in my Free Cyberguy Report Bulletin Cyberguy.com/newsletter
Ask a question to Kurt or to know what stories you would like to cover
Follow Kurt in their social channels
Answers to Cyberguy Questions Most Failed:
New of Kurt:
Copyright 2025 cyberguy.com. All rights reserved.
#login #alert #real #scam
Image Source : www.foxnews.com
